Hash Function Hash tables
Hash Function Hash tables - Search results - Wiki Hash Function Hash Tables
The page "Hash+Function+Hash+tables" does not exist. You can create a draft and submit it for review or request that a redirect be created, but consider checking the search results below to see whether the topic is already covered.
- checksum. Hash function security summary Secure Hash Algorithms NIST hash function competition Key derivation functions (category) "Hash functions". www.azillionmonkeys...
- cryptography, Whirlpool (sometimes styled WHIRLPOOL) is a cryptographic hash function. It was designed by Vincent Rijmen (co-creator of the Advanced Encryption...
 A cryptographic hash function (CHF) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size of n {\displaystyle...
A cryptographic hash function (CHF) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size of n {\displaystyle...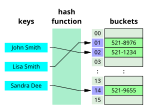 data type that maps keys to values. A hash table uses a hash function to compute an index, also called a hash code, into an array of buckets or slots...
data type that maps keys to values. A hash table uses a hash function to compute an index, also called a hash code, into an array of buckets or slots...- BLAKE is a cryptographic hash function based on Daniel J. Bernstein's ChaCha stream cipher, but a permuted copy of the input block, XORed with round constants...
 a hash function are called hash values, hash codes, hash digests, digests, or simply hashes. The values are usually used to index a fixed-size table called...
a hash function are called hash values, hash codes, hash digests, digests, or simply hashes. The values are usually used to index a fixed-size table called... worst-case access time. A perfect hash function can, as any hash function, be used to implement hash tables, with the advantage that no collision resolution has...
worst-case access time. A perfect hash function can, as any hash function, be used to implement hash tables, with the advantage that no collision resolution has...- The following tables compare general and technical information for a number of cryptographic hash functions. See the individual functions' articles for...
- to a spate of "hash flooding" denial-of-service attacks (HashDoS) in late 2011. SipHash is designed as a non-cryptographic hash function. Although it can...
 A distributed hash table (DHT) is a distributed system that provides a lookup service similar to a hash table. Key–value pairs are stored in a DHT, and...
A distributed hash table (DHT) is a distributed system that provides a lookup service similar to a hash table. Key–value pairs are stored in a DHT, and...- is a non-cryptographic hash function created by Glenn Fowler, Landon Curt Noll, and Kiem-Phong Vo. The basis of the FNV hash algorithm was taken from...
- cryptographic hash function designed by Ross Anderson and Eli Biham in 1995 for efficiency on 64-bit platforms. The size of a Tiger hash value is 192 bits...
- hash >> 6; } hash += hash << 3; hash ^= hash >> 11; hash += hash << 15; return hash; } Sample hash values for one_at_a_time hash function. one_at_a_time("a"...
 computer science, a hash collision or hash clash is when two distinct pieces of data in a hash table share the same hash value. The hash value in this case...
computer science, a hash collision or hash clash is when two distinct pieces of data in a hash table share the same hash value. The hash value in this case...- The MD2 Message-Digest Algorithm is a cryptographic hash function developed by Ronald Rivest in 1989. The algorithm is optimized for 8-bit computers....
- A rolling hash (also known as recursive hashing or rolling checksum) is a hash function where the input is hashed in a window that moves through the input...
- cryptographic hash functions. Note that not all entries may be up to date. For a summary of other hash function parameters, see comparison of cryptographic hash functions...
- ShangMi 3 (SM3) is a cryptographic hash function used in the Chinese National Standard. It was published by the National Cryptography Administration (Chinese:...
- building hash tables from the tuples of one or both of the joined relations, and subsequently probing those tables so that only tuples with the same hash code...
 Skein is a cryptographic hash function and one of five finalists in the NIST hash function competition. Entered as a candidate to become the SHA-3 standard...
Skein is a cryptographic hash function and one of five finalists in the NIST hash function competition. Entered as a candidate to become the SHA-3 standard...
- hashtable English Wikipedia has an article on: hash table Wikipedia hashtable hash table (plural hash tables) (programming) An associative array implemented
- Wine-Barrel.—List of Things to Make Rum.—Things to Color It With.—Canal-Boat Hash.—English Adulteration Law.—Effects of Drugs Used.—How To Use Them.—Buying
- work, rats */ hash.c. #else /* !STDSTDIO */ /* The big, slow, and stupid way */ str.c. /* This bit of chicanery makes a unary function followed by a parenthesis
- { hash += (b & 0xFF); hash += (hash << 10); hash ^= (hash >>> 6); } hash += (hash << 3); hash ^= (hash >>> 11); hash += (hash << 15); return hash; }





