Diffie–Hellman Key Exchange Security
Diffie–Hellman Key Exchange Security - Search results - Wiki Diffie–Hellman Key Exchange Security
The page "Diffie–Hellman+Key+Exchange+Security" does not exist. You can create a draft and submit it for review or request that a redirect be created, but consider checking the search results below to see whether the topic is already covered.
 Diffie–Hellman (DH) key exchange is a mathematical method of securely exchanging cryptographic keys over a public channel and was one of the first public-key...
Diffie–Hellman (DH) key exchange is a mathematical method of securely exchanging cryptographic keys over a public channel and was one of the first public-key...- Elliptic-curve Diffie–Hellman (ECDH) is a key agreement protocol that allows two parties, each having an elliptic-curve public–private key pair, to establish...
- DNSSEC) ‒ and a Diffie–Hellman key exchange to set up a shared session secret from which cryptographic keys are derived. In addition, a security policy for...
 cryptographic keys, that helped solve key distribution—a fundamental problem in cryptography. Their technique became known as Diffie–Hellman key exchange. The...
cryptographic keys, that helped solve key distribution—a fundamental problem in cryptography. Their technique became known as Diffie–Hellman key exchange. The... Whitfield Diffie and Martin Hellman published a cryptographic protocol called the Diffie–Hellman key exchange (D–H) based on concepts developed by Hellman's PhD...
Whitfield Diffie and Martin Hellman published a cryptographic protocol called the Diffie–Hellman key exchange (D–H) based on concepts developed by Hellman's PhD...- Post-Quantum Extended Diffie-Hellman (PQXDH) is a Kyber-based post-quantum cryptography upgrade to the Diffie–Hellman key exchange. It is notably being...
- keys are dead, said: "The answer to that question is an unqualified yes." The 2015 Logjam attack revealed additional dangers in using Diffie-Hellman key...
- theoretical basis of the Diffie–Hellman key exchange and its derivatives. The motivation for this problem is that many security systems use one-way functions:...
- isogeny Diffie–Hellman key exchange (SIDH or SIKE) is an insecure proposal for a post-quantum cryptographic algorithm to establish a secret key between...
 known as Diffie–Hellman key exchange, although Hellman has argued that it ought to be called Diffie-Hellman-Merkle key exchange because of Merkle's separate...
known as Diffie–Hellman key exchange, although Hellman has argued that it ought to be called Diffie-Hellman-Merkle key exchange because of Merkle's separate...- Logjam is a security vulnerability in systems that use Diffie–Hellman key exchange with the same prime number. It was discovered by a team of computer...
 Layer Security (TLS), SSH, S/MIME and PGP. Some public key algorithms provide key distribution and secrecy (e.g., Diffie–Hellman key exchange), some...
Layer Security (TLS), SSH, S/MIME and PGP. Some public key algorithms provide key distribution and secrecy (e.g., Diffie–Hellman key exchange), some...- used key exchange algorithms. In 1976, Whitfield Diffie and Martin Hellman constructed the Diffie–Hellman algorithm, which was the first public key algorithm...
- Forward secrecy (redirect from Non-interactive key exchange)typically uses an ephemeral Diffie–Hellman key exchange to prevent reading past traffic. The ephemeral Diffie–Hellman key exchange is often signed by the server...
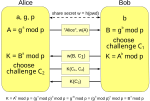 a brute force attack on the stolen data). A version of EKE based on Diffie–Hellman, known as DH-EKE, has survived attack and has led to improved variations...
a brute force attack on the stolen data). A version of EKE based on Diffie–Hellman, known as DH-EKE, has survived attack and has led to improved variations...- generate a unique session key for subsequent encryption and decryption of data during the session, or uses Diffie–Hellman key exchange (or its variant elliptic-curve...
- illustrates the attack of an eavesdropper in the Diffie–Hellman key exchange protocol to obtain the exchanged secret key. Consider a cyclic group G of order q....
- The decisional Diffie–Hellman (DDH) assumption is a computational hardness assumption about a certain problem involving discrete logarithms in cyclic groups...
- necessity for using a key exchange protocol like Diffie-Hellman key exchange. Another method of key exchange involves encapsulating one key within another. Typically...
- IPsec (redirect from Encapsulating Security Payload)the NSA compromised IPsec VPNs by undermining the Diffie-Hellman algorithm used in the key exchange. In their paper, they allege the NSA specially built...
- in advance of the communication. Diffie-Hellman in particular provides a convenient way to establish a symmetric key that can then provide a convenient
- security relies on the discrete logarithm problem, which is still thought to be difficult. Diffie-Hellman is generally used to generate a unique key by





