Cryptographic Protocol Examples
Cryptographic Protocol Examples - Search results - Wiki Cryptographic Protocol Examples
The page "Cryptographic+Protocol+Examples" does not exist. You can create a draft and submit it for review or request that a redirect be created, but consider checking the search results below to see whether the topic is already covered.
- A cryptographic protocol is an abstract or concrete protocol that performs a security-related function and applies cryptographic methods, often as sequences...
- Cryptographic primitives are well-established, low-level cryptographic algorithms that are frequently used to build cryptographic protocols for computer...
 In cryptography, a nonce is an arbitrary number that can be used just once in a cryptographic communication. It is often a random or pseudo-random number...
In cryptography, a nonce is an arbitrary number that can be used just once in a cryptographic communication. It is often a random or pseudo-random number... Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a...
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a...- In cryptography, a key-agreement protocol is a protocol whereby two or more parties can agree on a cryptographic key in such a way that both influence...
- Quantum cryptography is the science of exploiting quantum mechanical properties to perform cryptographic tasks. The best known example of quantum cryptography...
- Transport Layer Security (redirect from Transport Layer Security Protocol)Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network. The protocol is widely used in applications...
- IPsec (redirect from Internet Protocol Security)Management Protocol (ISAKMP) RFC 4307: Cryptographic Algorithms for Use in the Internet Key Exchange Version 2 (IKEv2) RFC 4308: Cryptographic Suites for...
- Cryptographically Generated Address (CGA) is an Internet Protocol Version 6 (IPv6) address that has a host identifier computed from a cryptographic hash...
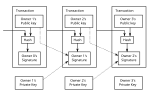 create new bitcoins and verify transactions; and cryptographic security. Users broadcast cryptographically signed messages to the network using Bitcoin cryptocurrency...
create new bitcoins and verify transactions; and cryptographic security. Users broadcast cryptographically signed messages to the network using Bitcoin cryptocurrency... Digital signature (redirect from Cryptographic signature)the recipient. Digital signatures are a standard element of most cryptographic protocol suites, and are commonly used for software distribution, financial...
Digital signature (redirect from Cryptographic signature)the recipient. Digital signatures are a standard element of most cryptographic protocol suites, and are commonly used for software distribution, financial... Diffie–Hellman key exchange (redirect from New Directions in Cryptography)mathematical method of securely exchanging cryptographic keys over a public channel and was one of the first public-key protocols as conceived by Ralph Merkle and...
Diffie–Hellman key exchange (redirect from New Directions in Cryptography)mathematical method of securely exchanging cryptographic keys over a public channel and was one of the first public-key protocols as conceived by Ralph Merkle and...- Secure Shell (redirect from Secure Shell Protocol)The Secure Shell Protocol (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Its most notable...
- An authentication protocol is a type of computer communications protocol or cryptographic protocol specifically designed for transfer of authentication...
- Challenge–response authentication (redirect from Challenge (Cryptography))authentication protocol Challenge–response spam filtering CRAM-MD5 Cryptographic hash function Cryptographic nonce Kerberos Otway–Rees protocol Needham–Schroeder...
 Most cryptographic hash functions are designed to take a string of any length as input and produce a fixed-length hash value. A cryptographic hash function...
Most cryptographic hash functions are designed to take a string of any length as input and produce a fixed-length hash value. A cryptographic hash function...- The Time-Stamp Protocol, or TSP is a cryptographic protocol for certifying timestamps using X.509 certificates and public key infrastructure. The timestamp...
 Interoperability Protocol (KMIP) is an extensible communication protocol that defines message formats for the manipulation of cryptographic keys on a key...
Interoperability Protocol (KMIP) is an extensible communication protocol that defines message formats for the manipulation of cryptographic keys on a key...- allows both providing random uniformly distributed cryptographic keys and generating cryptographic keys from a password supplied by the user. The risk...
 HTTPS (redirect from Hypertext Transfer Protocol (Secure))cryptographic attack.[citation needed] Because TLS operates at a protocol level below that of HTTP and has no knowledge of the higher-level protocols...
HTTPS (redirect from Hypertext Transfer Protocol (Secure))cryptographic attack.[citation needed] Because TLS operates at a protocol level below that of HTTP and has no knowledge of the higher-level protocols...
- asymmetric encryption schemes like RSA have for many years provided cryptographic security to settings in which two users, Alice and Bob, must communicate
- and came up with a relatively simple improvement to a widely used cryptographic primitive. I spent a month or two writing it up (along with relevant
- sometimes called a keyed (cryptographic) hash function. Protocols Authentication protocols e.g. Kerberos Key exchange protocols Diffie-Hellman Secure Communications







