Peer-To-Peer Chord
In computing, Chord is a protocol and algorithm for a peer-to-peer distributed hash table.
A distributed hash table stores key-value pairs by assigning keys to different computers (known as "nodes"); a node will store the values for all the keys for which it is responsible. Chord specifies how keys are assigned to nodes, and how a node can discover the value for a given key by first locating the node responsible for that key.
Chord is one of the four original distributed hash table protocols, along with CAN, Tapestry, and Pastry. It was introduced in 2001 by Ion Stoica, Robert Morris, David Karger, Frans Kaashoek, and Hari Balakrishnan, and was developed at MIT. The 2001 Chord paper won an ACM SIGCOMM Test of Time award in 2011.
Subsequent research by Pamela Zave has shown that the original Chord algorithm (as specified in the 2001 SIGCOMM paper, the 2001 Technical report, the 2002 PODC paper, and the 2003 TON paper ) can mis-order the ring, produce several rings, and break the ring.
Overview

Nodes and keys are assigned an 
Using the Chord lookup protocol, nodes and keys are arranged in an identifier circle that has at most 



Each node has a successor and a predecessor. The successor to a node is the next node in the identifier circle in a clockwise direction. The predecessor is counter-clockwise. If there is a node for each possible ID, the successor of node 0 is node 1, and the predecessor of node 0 is node 
The concept of successor can be used for keys as well. The successor node of a key 





Since the successor (or predecessor) of a node may disappear from the network (because of failure or departure), each node records an arc of 


Protocol details

Basic query
The core usage of the Chord protocol is to query a key from a client (generally a node as well), i.e. to find 


Finger table
To avoid the linear search above, Chord implements a faster search method by requiring each node to keep a finger table containing up to 







With such a finger table, the number of nodes that must be contacted to find a successor in an N-node network is 
Node join
Whenever a new node joins, three invariants should be maintained (the first two ensure correctness and the last one keeps querying fast):
- Each node's successor points to its immediate successor correctly.
- Each key is stored in
.
- Each node's finger table should be correct.
To satisfy these invariants, a predecessor field is maintained for each node. As the successor is the first entry of the finger table, we do not need to maintain this field separately any more. The following tasks should be done for a newly joined node 
- Initialize node
(the predecessor and the finger table).
- Notify other nodes to update their predecessors and finger tables.
- The new node takes over its responsible keys from its successor.
The predecessor of 







Stabilization
To ensure correct lookups, all successor pointers must be up to date. Therefore, a stabilization protocol is running periodically in the background which updates finger tables and successor pointers.
The stabilization protocol works as follows:
- Stabilize(): n asks its successor for its predecessor p and decides whether p should be n's successor instead (this is the case if p recently joined the system).
- Notify(): notifies n's successor of its existence, so it can change its predecessor to n
- Fix_fingers(): updates finger tables
Potential uses
- Cooperative Mirroring: A load balancing mechanism by a local network hosting information available to computers outside of the local network. This scheme could allow developers to balance the load between many computers instead of a central server to ensure availability of their product.
- Time-shared storage: In a network, once a computer joins the network its available data is distributed throughout the network for retrieval when that computer disconnects from the network. As well as other computers' data is sent to the computer in question for offline retrieval when they are no longer connected to the network. Mainly for nodes without the ability to connect full-time to the network.
- Distributed Indices: Retrieval of files over the network within a searchable database. e.g. P2P file transfer clients.
- Large scale combinatorial searches: Keys being candidate solutions to a problem and each key mapping to the node, or computer, that is responsible for evaluating them as a solution or not. e.g. Code Breaking
- Also used in wireless sensor networks for reliability
Proof sketches
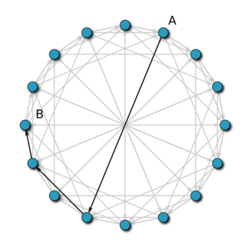
With high probability, Chord contacts 

Suppose node 
























This process of halving the remaining distance repeats itself, so after 







If Chord keeps track of 
Simply, the probability that all 

Pseudocode
- Definitions for pseudocode
-
- finger[k]
- first node that succeeds
- successor
- the next node from the node in question on the identifier ring
- predecessor
- the previous node from the node in question on the identifier ring
The pseudocode to find the successor node of an id is given below:
// ask node n to find the successor of id n.find_successor(id) // Yes, that should be a closing square bracket to match the opening parenthesis. // It is a half closed interval. if id ∈ (n, successor] then return successor else // forward the query around the circle n0 := closest_preceding_node(id) return n0.find_successor(id) // search the local table for the highest predecessor of id n.closest_preceding_node(id) for i = m downto 1 do if (finger[i] ∈ (n, id)) then return finger[i] return n
The pseudocode to stabilize the chord ring/circle after node joins and departures is as follows:
// create a new Chord ring. n.create() predecessor := nil successor := n // join a Chord ring containing node n'. n.join(n') predecessor := nil successor := n'.find_successor(n) // called periodically. n asks the successor // about its predecessor, verifies if n's immediate // successor is consistent, and tells the successor about n n.stabilize() x = successor.predecessor if x ∈ (n, successor) then successor := x successor.notify(n) // n' thinks it might be our predecessor. n.notify(n') if predecessor is nil or n'∈(predecessor, n) then predecessor := n' // called periodically. refreshes finger table entries. // next stores the index of the finger to fix n.fix_fingers() next := next + 1 if next > m then next := 1 finger[next] := find_successor(n+2next-1); // called periodically. checks whether predecessor has failed. n.check_predecessor() if predecessor has failed then predecessor := nil
See also
References
External links
- The Chord Project (redirect from: http://pdos.lcs.mit.edu/chord/)
- Open Chord – An Open Source Java Implementation
- Chordless – Another Open Source Java Implementation
- jDHTUQ- An open source java implementation. API to generalize the implementation of peer-to-peer DHT systems. Contains GUI in mode data structure
This article uses material from the Wikipedia English article Chord (peer-to-peer), which is released under the Creative Commons Attribution-ShareAlike 3.0 license ("CC BY-SA 3.0"); additional terms may apply (view authors). Content is available under CC BY-SA 4.0 unless otherwise noted. Images, videos and audio are available under their respective licenses.
®Wikipedia is a registered trademark of the Wiki Foundation, Inc. Wiki English (DUHOCTRUNGQUOC.VN) is an independent company and has no affiliation with Wiki Foundation.
